Organizations just need to watch the news to know that cybersecurity breaches are becoming an increasingly common threat to the healthcare industry. According to the U.S. Department of Health and Human Services (HHS), 45 million records were compromised by healthcare cybersecurity attacks in 2021, up more than 3x as much from 14 million in 2018.
Many of these attacks arose during the pandemic as the transition to remote work provided hackers with countless new vulnerabilities to target and exploit. In response, as many as 48% of healthcare industry executives said they were increasing their cybersecurity budgets in 2021. With attack rates still increasing well into 2022, it’s critical that businesses remain informed on current best practices in order to protect both themselves and their patients.
Anti-ransomware measures
Over the past couple of years, ransomware has grown increasingly popular amongst cybercriminal groups, with 42% of healthcare organizations reporting at least two attacks within the past two years. Whereas data recovery might mitigate the ransomware risk in other industries, ransomware attacks in the healthcare industry can result in longer length-of-stays, poor patient outcomes, and complications in medical procedures.
Unfortunately, the high stakes nature of successful cybersecurity attacks in healthcare means many organizations are more likely to a pay premium, and within a much shorter time frame.
In an effort to reduce some of the risks associated with such attacks, many businesses are investing more in protective measures such multi-factor authentication (MFA), which in itself has become a requirement for many cyber insurance companies. Other organizations are making use of immutable backups to provide a protective layer between their current systems and a potential restore point. Immutable backups function as a separate copy with their own security protocols, similar to a safety deposit box.
Securing medical devices
Internet of Things (IoT) devices have exploded in popularity over the last few years due to their versatility and wide range of applications, with the market projected to reach $534.3 billion by 2025. However, with all that recent growth also comes a surplus of new targets for potential hackers hoping to capitalize on their portability and internet access.
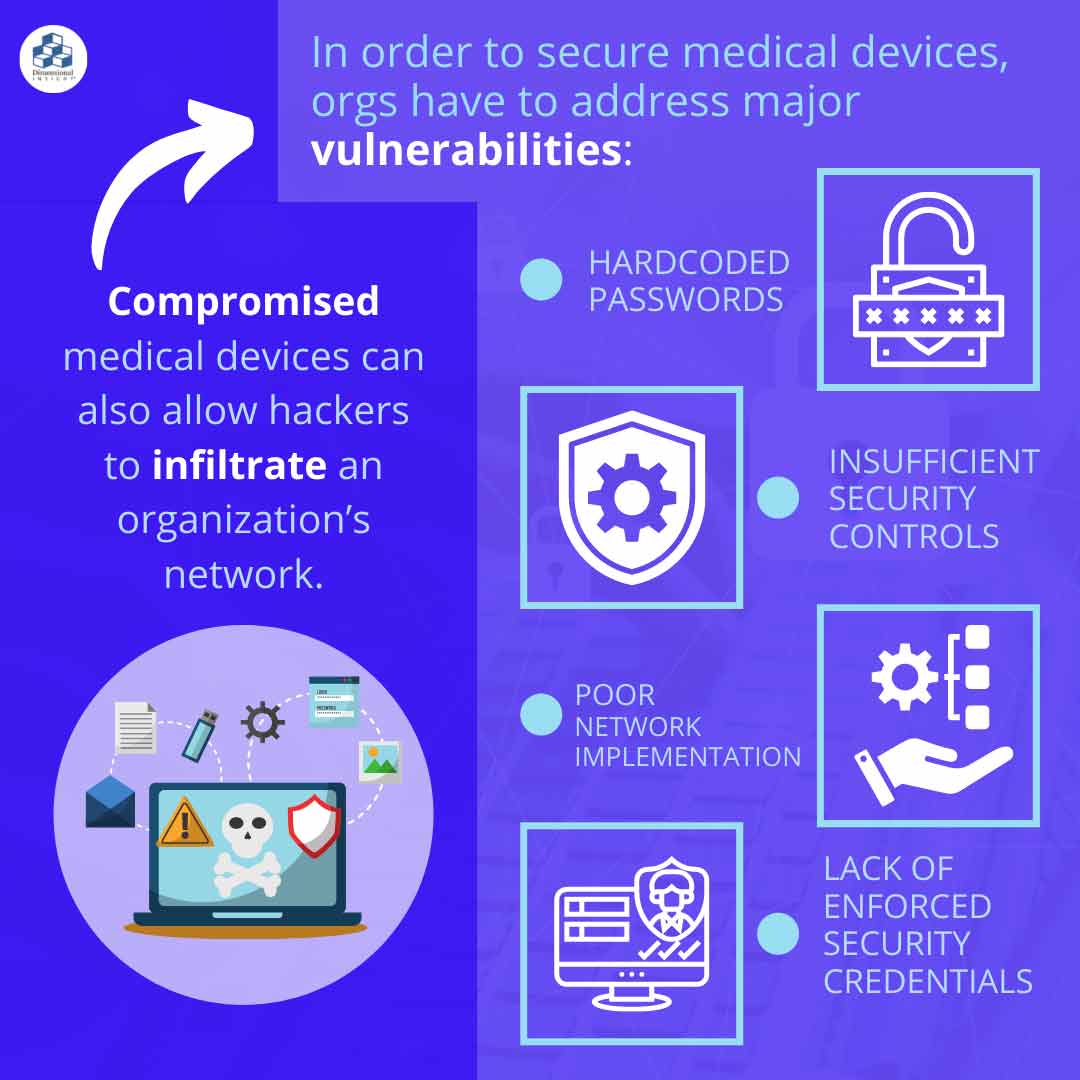
On top of the danger posed to patients, compromised medical devices can also allow hackers to infiltrate an organization’s network. In order to secure medical devices from would-be criminals, organizations have to address major vulnerabilities such as hardcoded passwords, insufficient security controls, poor network implementation, and a lack of enforced security credentials.
As these devices age, health systems will also need to implement a top-down approach to security to ensure that legacy devices aren’t compromised. Part of this will entail developing a bridge program to determine how aging devices should be managed before they’re replaced. Furthermore, increased monitoring would provide useful metrics related to the device lifecycle and allow organizations to better plan for future devices.
Protecting supply chains
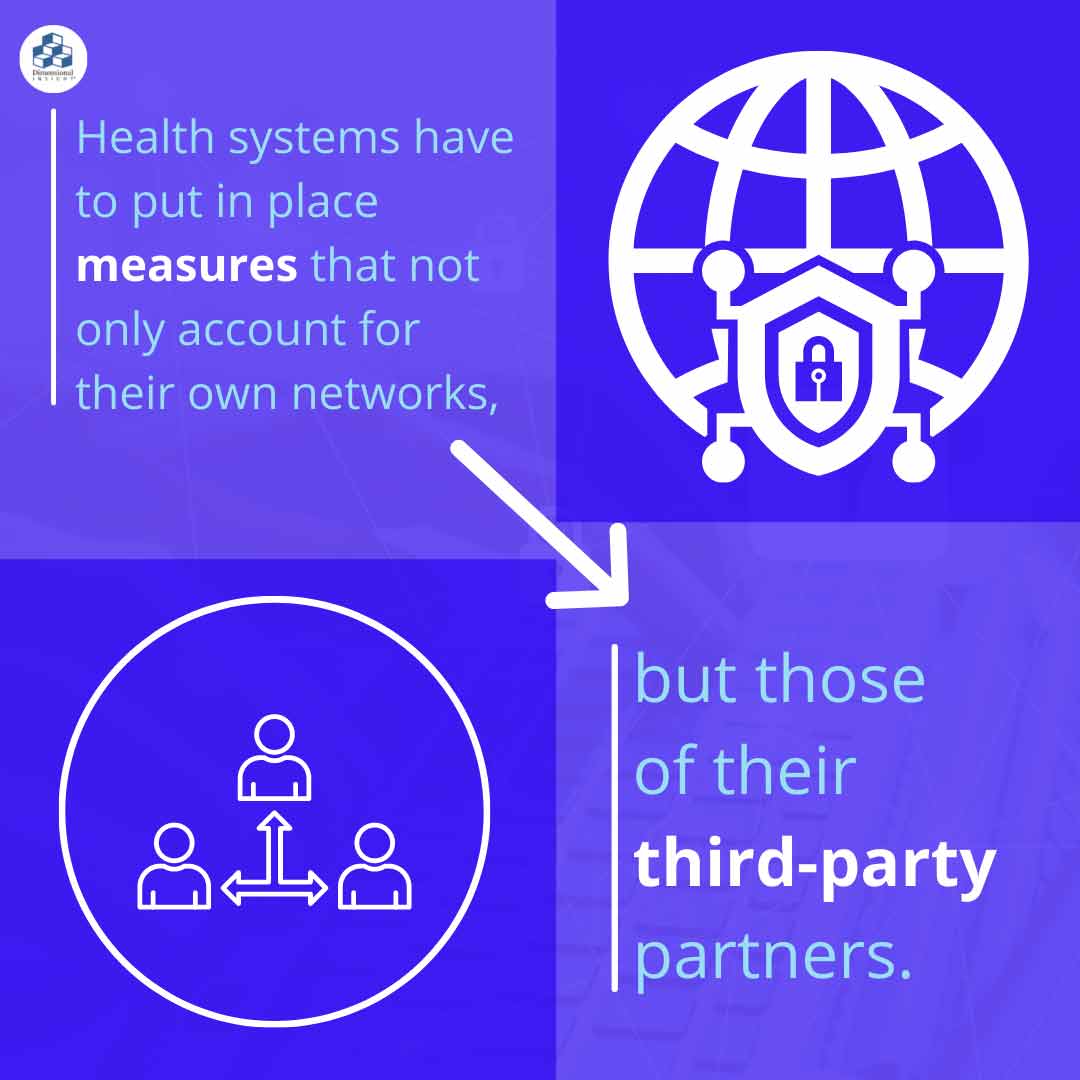
Over the past couple years, large-scale attacks like the SolarWinds incident demonstrated just how devastating supply chain breaches can be for the businesses they support. With the number of third-party platforms being used by businesses nowadays, health systems have to put in place measures that not only account for their own networks, but those of their third-party partners.
First and foremost, organizations have to assess and know the risks associated with their suppliers. Security is only as strong as its weakest link, and holding themselves to high standards of cybersecurity means little if healthcare systems don’t apply these same standards to the third-party groups they work with. Every connection an organization makes is a potential new endpoint for criminals to attack.
Reliable suppliers, coupled with preemptive measures like vendor access monitoring, continuous vulnerability/risk assessments, background checks, and regulatory compliance requirements can go a long way in terms of deterring potential attacks. However, the risk is never zero when it comes to cybersecurity, and healthcare systems need to include their supply chain in their response and remediation plan. In the case that an incident occurs, organizations need to be ready and be able to communicate and work together with their supplies to address breaches and mitigate any further damages.
Increased monitoring and risk assessments
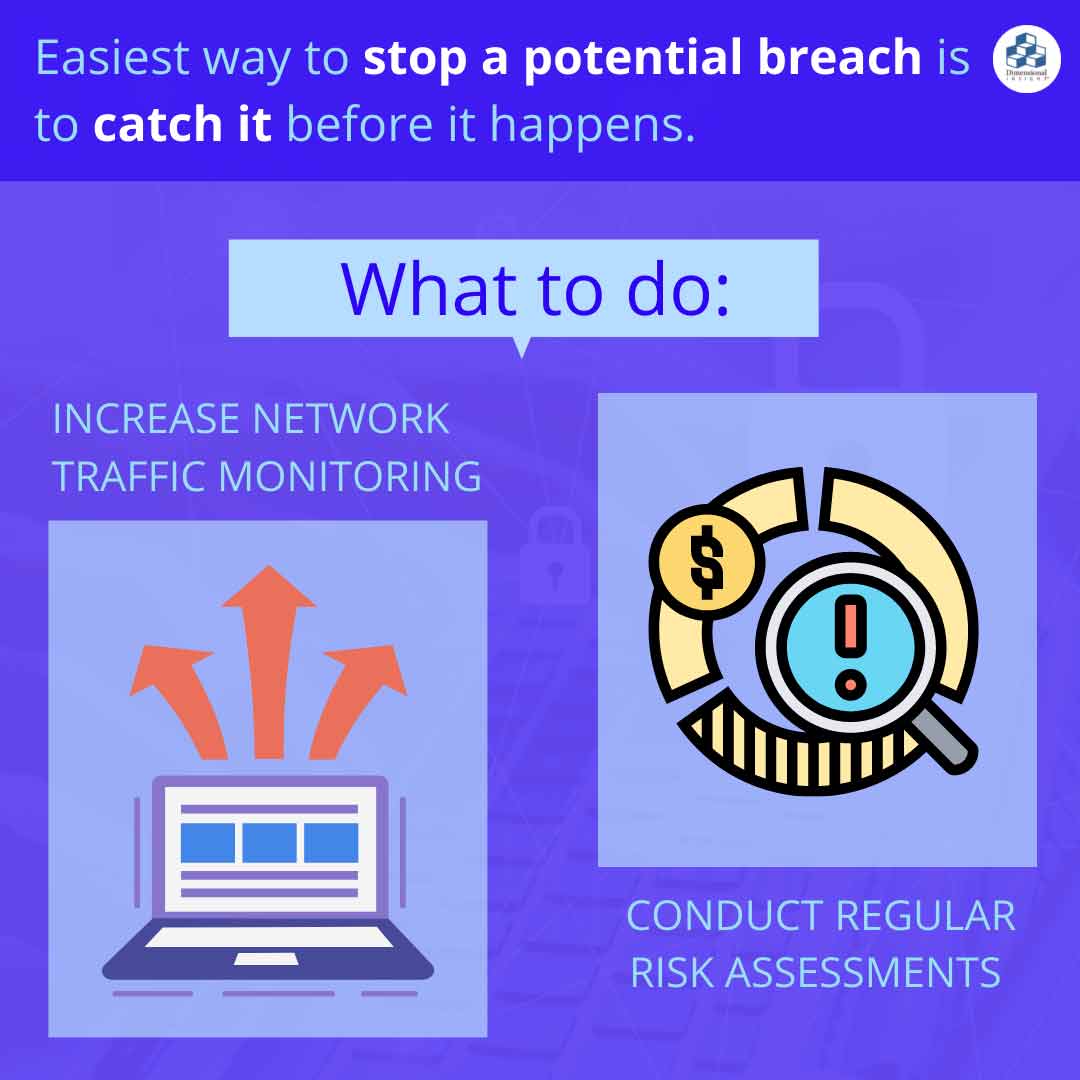
The easiest way to stop a potential breach is to catch it before it happens. Increased network traffic monitoring, especially with the transition to remote work during the pandemic, is crucial for making sure that potential risks are never realized. This is why many healthcare organizations are investing more and more in solutions that provide services like network perimeter protection, network surveillance, and appropriate network access assurance. Full network visibility is also becoming increasingly popular across the healthcare IT landscape.
Conducting regular risk assessments can also help healthcare providers detect dangerous vulnerabilities long before criminals do. With new weak points constantly emerging as organizations update and change their systems, IT departments have to remain proactive about evaluating potential threats.
Education and advocacy
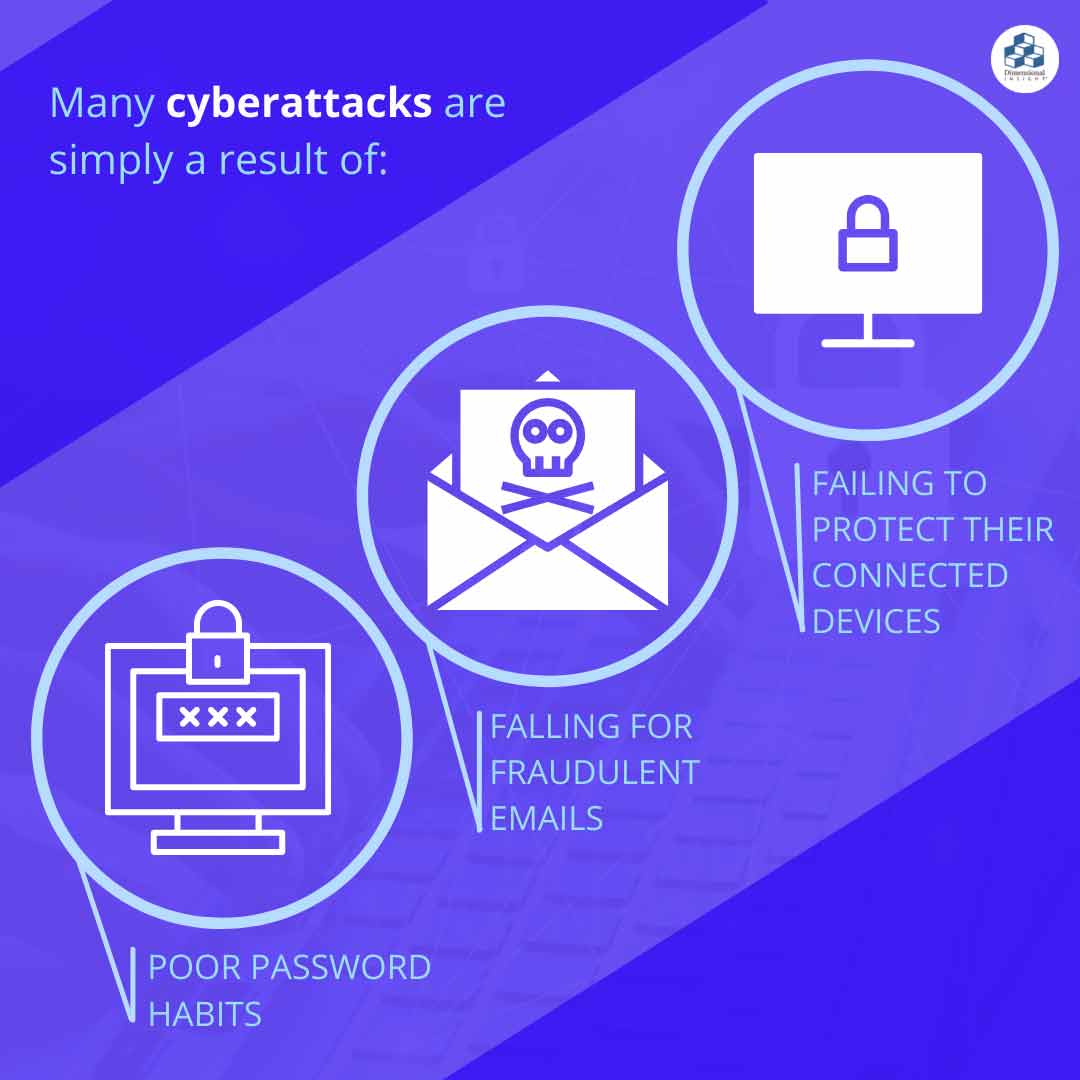
At the end of the day, cybersecurity often comes down to the individual employee. Many attacks are simply a result of poor password habits, falling for fraudulent emails, and failing to protect their connected devices. End-user education on best practices and advocacy from upper management is an easy and cheap way to dramatically reduce some of the risks facing healthcare organizations.
IT departments need to establish and enforce policies that clearly communicate appropriate use of an organization’s systems and data. Human-error is often the biggest threat to cybersecurity, and even small improvements in proper network access can go a long way. Remember, a phishing email is only as dangerous as the individual who opens it.
What now?
Technology is constantly evolving and so are the criminals seeking to exploit it. The healthcare industry will continue to be a hot target for cybersecurity attacks for years to come, and organizations have to prepare accordingly. To learn more the current state of healthcare technology following the pandemic, check out our blog post—”Top Healthcare BI Trends.”
- How Spirits Brands Can Improve Brand Loyalty with Data Analytics - January 30, 2024
- The Collapse of Herbl, and How Other Cannabis Distributors Can Avoid the Same Fate - January 24, 2024
- Top 5 Blog Posts of 2023 - December 28, 2023




