Consumers have grown accustomed to online hacks that affect credit cards or personal information, but after a recent hack of a Florida’s town’s water supply and a Texas gas line, a new fear has arisen…as well as a new frontier to protect.
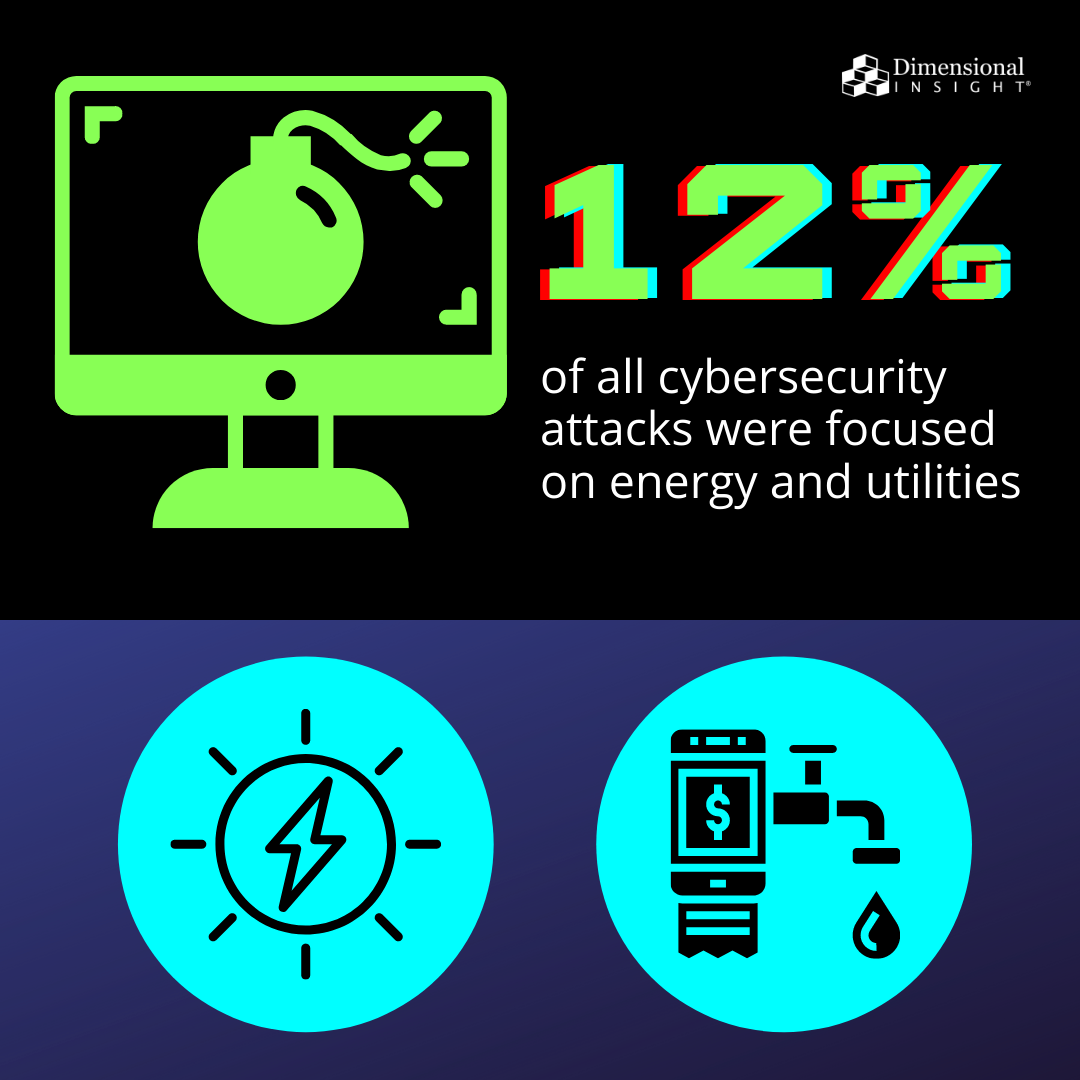
In 2021, 12% of all cybersecurity attacks were focused on energy and utilities, according to Cobalt.
Cybersecurity experts have long warned that insecure remote work software presents a significant source of weakness vulnerable to hacking. Hacking utilities can be inconvenient at best or dangerous and deadly at worst.
Technology will only continue to control more of the utility space, but what are the risks?
Recent hackings pose public health issues

Earlier this year, hackers jeopardized the water supply of Oldsmar, Florida, gaining access to a water treatment facility by using a dormant remote access software. In simpler terms, the bad guys weren’t even there when they took control of the precious water supply.
According to CNN, the treatment plant utilized multiple computers running on an aging version of Microsoft Windows to help monitor the facility remotely. All of the computers shared a single password to manage the plant.
The hackers briefly changed the levels of lye in the drinking water—which could have poisoned the drinking water of thousands of Florida residents.
Sheriff Bob Gualtieri of Pinellas County said in a press conference following the event that the level of sodium hydroxide—the main ingredient in drain cleaner—was changed from 100 parts per million to 11,100 parts per million. If the 15,000 residents of Oldsmar drank the water at this level, they could have been poisoned.
“This is dangerous stuff,” Mr. Gualtieri said. “It’s a bad act. It’s a bad actor. It’s not just a little chlorine or a little fluoride—you’re basically talking about lye.”
The cyber breach lasted less than 5 minutes, and luckily the town averted danger.
In the past, “You had to get past the guards with the guns, the fences, the video cameras, all the physical security measures in order to get access,” Eric Cole, a former CIA cybersecurity expert and author of the upcoming book Cyber Crisis told CNN. But 2020 forced the majority of Americans to work from home. “These systems were never designed for that purpose, and proper security was never put in place.”
“I think what this shows us is it doesn’t matter who you are, whether you’re an individual, a small company or a large company, if you have vulnerabilities you’re going to be discovered, and you are a target, and cybersecurity is your responsibility,” Cole said.
Hacked gas pipeline causes run on pumps
Colonial Pipeline, the largest petroleum pipeline between Texas and New York, temporarily needed to shutter its operations after a ransomware attack in early May.
The private company admitted a hacker held its data hostage and demanded ransom to return access.
A shutdown of the 5,500-mile pipeline was another example of how the United States’ utilities face danger from cybersecurity breaches. The shutdown left airlines worried they’d be low on gas and average consumers sitting in line to ensure their gas tanks were filled.
“Even a temporary shutdown will likely drive already rising national retail gas prices over $3 per gallon for the first time since 2014,” Jay Hatfield, chief executive of Infrastructure Capital Management and an investor in natural gas and oil pipelines and storage, told The New York Times.
Within two days of the shutdown, the national average for a gallon of regular gasoline rose by 2 cents.
What utilities can do to protect themselves from hackers
Siemens and the Ponemon Institute released a report in 2019 stating 56% of utilities faced a cyberattack that year. So, more than half have already been put at risk.
Regardless if the utility is a public entity or a privately-held company, updating the software the system runs on and regularly running pen-tests can help protect against hackers and cybersecurity breaches.
Many companies may feel pressured to move operations to cloud-based solutions to accommodate remote work, but it’s essential not to migrate the data until it’s secure.
Investing in software that monitors for breaches can also help ensure any hacks are detected and quickly stopped.

- 87% of Utilities Have Experienced at Least One Data Breach in Last Three Years - February 5, 2024
- Can Drones Lower Your Next Utility Bill? - January 10, 2024
- Onshore Wind Farms Are The Next Big Thing In Renewable Energy - December 6, 2023



